
Image Credit: @artbytes via Bitlanders
According to Internet World Stats, there are already more than 4 billion Internet users all over the world since December of 2017. With almost half of these users coming from Asia.
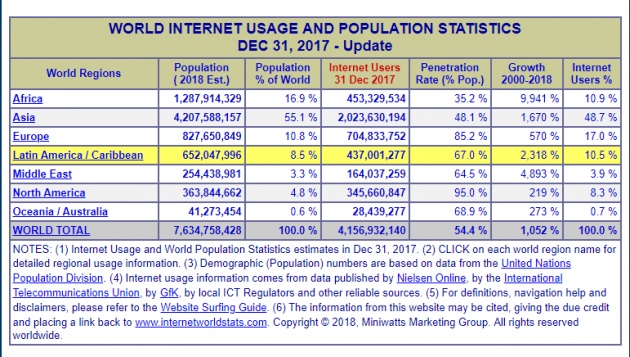
Image screenshot from https://www.internetworldstats.com/stats.htm
As the years go by, more and more people are enjoying the benefits of the continuous development of the Information and Communication Technologies. Communication has become cheaper. Sending a message across the globe these days would only take a few seconds. Photos and videos can be taken and shared almost instantly.
Internet Threats
How the development of technology does not come without a dark side. In my post, "How Safe Do You Think You Are on the Internet?", I mentioned several cyber threats that you might be exposed to on the Internet. Some of these are:
- Phishing
- Scams
- Cyberbullying
- Exposure to explicit contents
- Exposure Cyber predators
- Virus and Malware
Computer Virus and Malware Threats
In this post, I will focus more on Virus and Malware. First, let me clarify some common misconceptions about these two terms.
Malware, or malicious software, is any program or file that is harmful to a computer user. Malware includes computer viruses, worms, Trojan horses and spyware
As you may have noticed, a computer is a form of malware.
A computer virus is a type of malicious software that, when executed, replicates itself by modifying other computer programs and inserting its own code. When this replication succeeds, the affected areas are then said to be "infected" with a computer virus.
The term computer virus, however, has been commonly used by mistake to refer to other forms of malware like worms and trojan horses, which I will explain below.
Common Types of Malware

Image Credit: by kalhh via Pixabay
Computer Virus
As stated above, a virus replicates itself by inserting its own code with other computer programs. As a result, the infected programs will spread the virus to other programs when run. Different viruses will have different effects on a computer system. Some of the common symptoms are,
- the program would often crash
- your system would slow down
- Windows may shut down unexpectedly

Image Credit: by Geralt via Pixabay
Some viruses, however, are designed to be stealthy and may not exhibit any signs but may be designed to steal sensitive information.
Worm
These days, worms are often called a virus. However, the two has a distinct difference. While a virus needs a host program to infect to, a worm is a stand-alone program that replicates itself on your storage devices like your hard disks, flash drives, and may even replicate itself across the network.
Image Credit: @Zaadii via Pixabay
Worms may consume a lot of your computer resources, hide the files in your flash drives and replace them with a copy of itself or a link that would trigger the worm. Usually, these links are disguised with the names of your files.
Trojan Horse

Image Credit: https://informationstrategyrsm.files.wordpress.com/
Named after the giant wooden horse given as a gift to the people of Troy. Just as the horse in that famous story, a computer trojan horse disguises itself as a useful or entertaining program. Once run on a computer it will start doing other things in the background such as:
- download other malware
- steal information
- install a virus on your computer
- install other programs that you don't need
- Send emails using your email address as the sender
Spyware
Spyware is a form of malware that will gather information with the user knowing it. A spyware could gather data by actively monitoring keystrokes or the data you transmit and receive on the internet. A spyware is usually downloaded by a trojan horse.

Image Credit: @prettysleepy1 via Pixabay
Adware
Adware is a malicious program that is more annoying than damaging. Adware or short for Advertising Software is designed to deliver advertisements. These ads would often pop-up on your screen. However, some adware is known to come with a spyware as well.
Rootkit
A rootkit is a malware that is designed to enable unauthorized access to a computer. A rootkit could give an unrestricted 'root' or administrative access to a malicious party. This would allow the other party to execute programs, access information and even modify a security software. This makes rootkit one of the most difficult to detect.
BotWare/BotNet
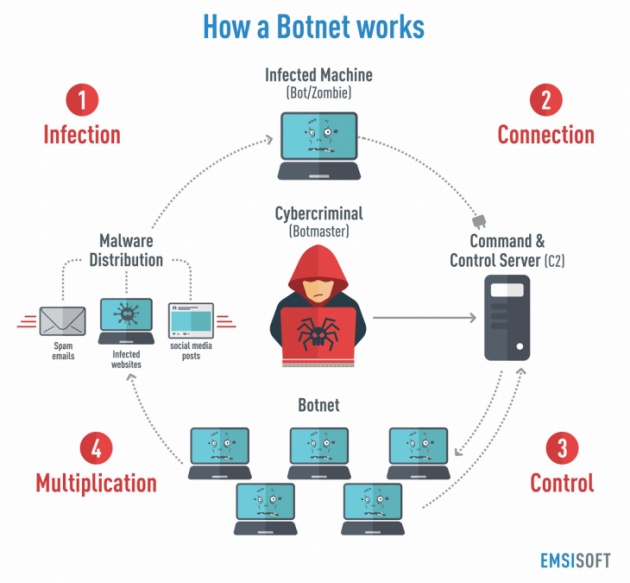
Image Credit: https://blog.emsisoft.com
A Botware is a malicious software that gives a malicious party access to your computer and its resources. Your computer or device, now turned into a Bot or a "Zombie", will then become part of a BotNet.
A BotNet is a collection of Internet-connected devices infected by a BotWare. Your device can then be used to launch a Distributed Denial of Service attack (DDoS) to a server or a network.
Ransomware

Image Credit: @geralt via Pixabay
A ransomware is a type of malicious software that denies you access to your data. A usual ransomware would encrypt your files and render them unreadable by the software that's supposed to read them. The victim would be able to regain access to their data by paying a certain amount within a limited time. If you could not send the said amount in time, the ransom could go up or ultimately delete your data.
However, security experts suggest not to pay the said Ransom. The attacker usually does not send the decryption key that's supposed to help you regain control of your files.
Personally, I was aware only of ransomware recently. A computer that was infected by a ransomware was referred to me. Unfortunately, the unit was already reformatted. The encrypted data was backed up. However, I believe the decryption tools made by several anti-malware companies are looking for a file or files within the system.
Rogue Security Software
One type of malware that often mislead users into believing that their system is infected by a virus is the rogue security software. Unsuspecting victims would download and install their scanner which would report a number of virus infections and would suggest that they pay for a fake full version in order to remove the virus. However, the fake removal tool would actually install other malware into their system.
Before we go the second part of this post, let me share with you this video again.
Video Credit: SciShow via YouTube
How do malware spread?

Image Credit @geralt via Pixabay
Different types of malware are spread using different means. In one way or another, every Internet users are exposed to these means. Most forms of malware were designed to spread with social engineering in mind. A malware could be delivered into your computer or device through at least one of the following:
- Malicious email attachment. Usually from a spam mail and from an unknown sender. However, someone you know might be a victim as well and the malware has sent an email from his device using his name as well.
- The Rogue Security Software mentioned above is actually a common way of downloading a malware onto your system.
- Drive-by-download. Drive-by download means an unintentional download of a malware to your computer. You don't have to click anything on a website in order to download a malware. It is an exploit on an un-updated browser and/or operating system. All you need is to drop by a compromised website and a code could be installed on your computer. In turn, it may download a malware from another source without you knowing it.
- Infected removable storage. Even if you are offline, you could still get infected by a malware. Worms are often spread through infected flash drives or USB.
- P2P Download. P2P or Peer to Peer. Meaning at least two computer systems are connected to each other via the Internet. Files can be shared directly without the need for a server. The danger here is if you are downloading a program from an infected source. Or the other party could be baiting a trojan horse. One common P2P example is torrent.
To explain further how malware and viruses work, watch this video.
video credit: SJ Smith via YouTube
Final Thoughts
The list about is just the common types of malware. There may be more than what I have listed here that I am not yet aware of and they may spread on other means not listed here. New malware comes up very frequently. Thus, having an updated anti-virus is not enough to protect our system. In my future post, I will outline some tips on how to keep our computers and devices safe from these threats.
Thanks for reading.
-o-o-O-O-O-0-0-0-O-O-O-o-o-
References:
- https://sgtomorrow.mcafee.com/consumer/family-safety/drive-by-download/
- https://en.wikipedia.org/wiki/Rogue_security_software
- https://www.comparitech.com/antivirus/types-of-malware/#gref
- https://blog.emsisoft.com/en/27233/what-is-a-botnet/
-o-o-O-O-O-0-0-0-O-O-O-o-o-
John Reynold Loberiza (a.k.a @artbytes) is a freelance graphic artist, web developer, and blogger. He is also a licensed Financial Adviser under Insular Life.
The content of this blog post is the author's original work. Proper credit is always given to the respective sources of information and images. Please feel free to check out my other blog posts: http://www.bitlanders.com/Artbytes/blog_post
If you have any reactions or inquiries regarding the subject of this post, please write it in the comment or send the author a private message.
For more information or questions you can also:
- Visit my personal blog: https://jrlcentral.xyz
- Follow me on Twitter: http://twitter.com/jrlcentral
- or email me at jrlcreativeideas@gmail.com
~°~°~°o0O0o°~°~°~
Join Bitlanders
If you are not a member of Bitlanders yet and you are a content creator- a writer, blogger, photographer, an artist or a hobbyist, you can earn from your creations (blog posts, photos, artworks, or videos) by uploading them in Bitlanders.
You can join Bitlanders by clicking this link-> http://bit.ly/Join_bitlanders



