A bug discovered by security researchers Eric Taylor and Blake Welsh can change a standard customer feedback system called Aptean SupportSoft into a method for hackers to grab passwords, credit card information and usernames. Taylor and Welsh have also been able to inject code into chat sessions that makes small windows appear when a customer service chat session is initiated.
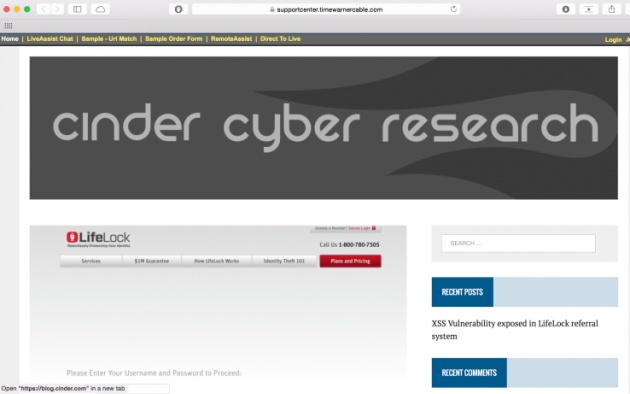
The exploit allows a hacker to add a bit of code to the end of a customer support URL ("http://VICTIM.com/sdcxuser/asp/frameset.asp?mainframe=//blog.cinder.com") that will then load another URL into the main “frame” of the website where the customer support chat screen usually appears. They have run the exploit on a number of sites including Comcast, Time Warner Cable, Sage, CGI and Cognizant. The exploit, called a cross-site scripting attack, has been tested on each of these sites.
The bug can be innocuous. For example, Taylor and Walsh were able to make their own blog appear on Time Warner’s customer support page.
However, hackers could use the same technique to grab user data. Here they have injected a fake login page hosted on their own server: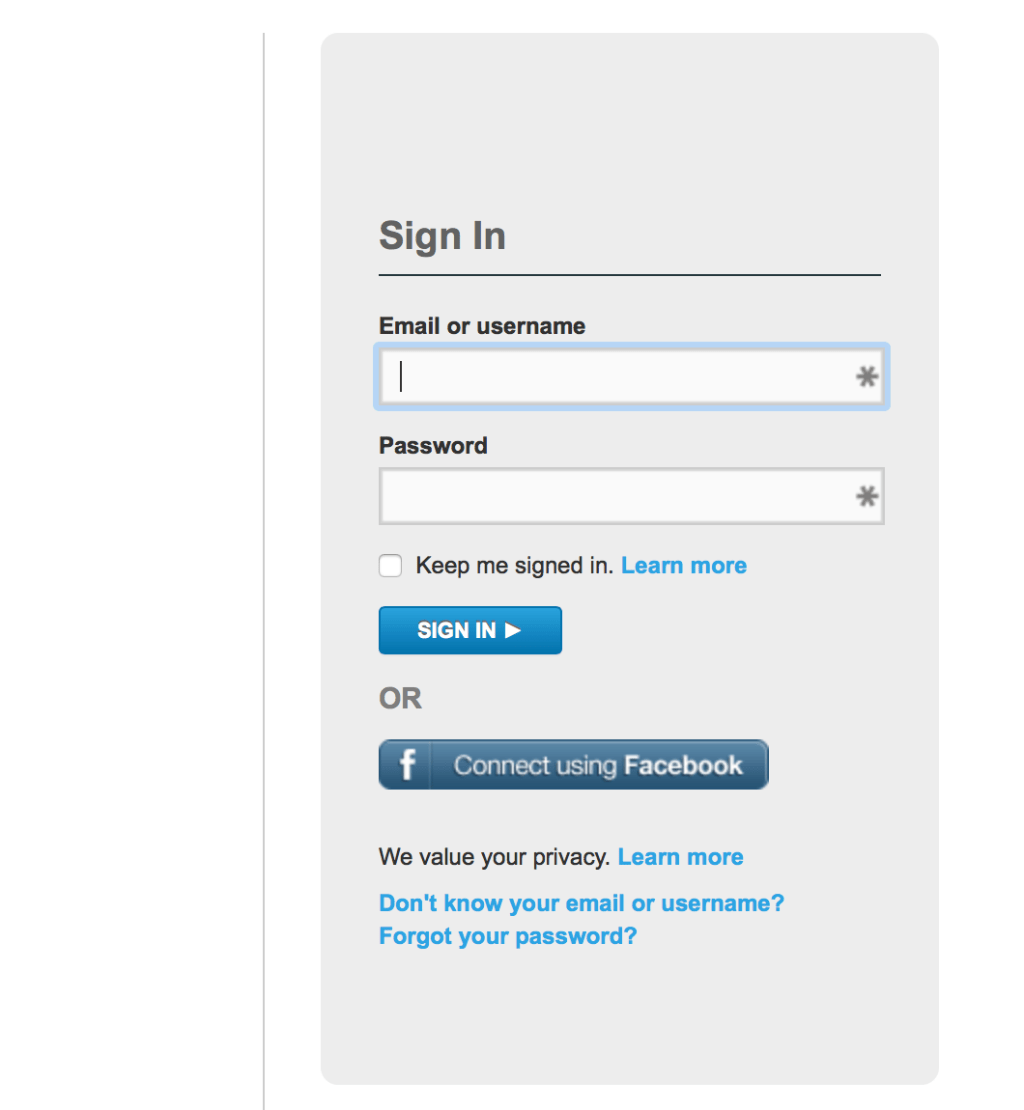
Into Xfinity’s customer support page: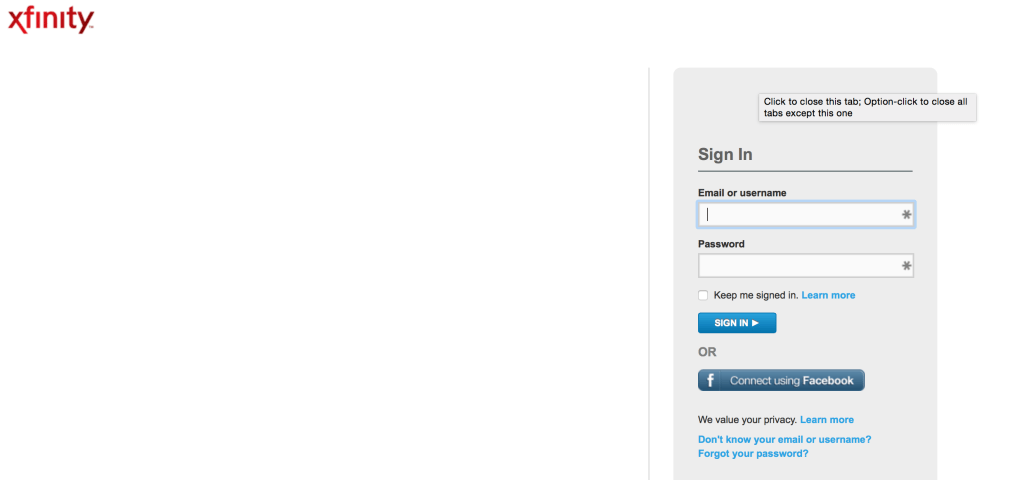
Finally, they were able to create a dangerous phishing exploit by masquerading as a page served by Comcast’s secure servers.
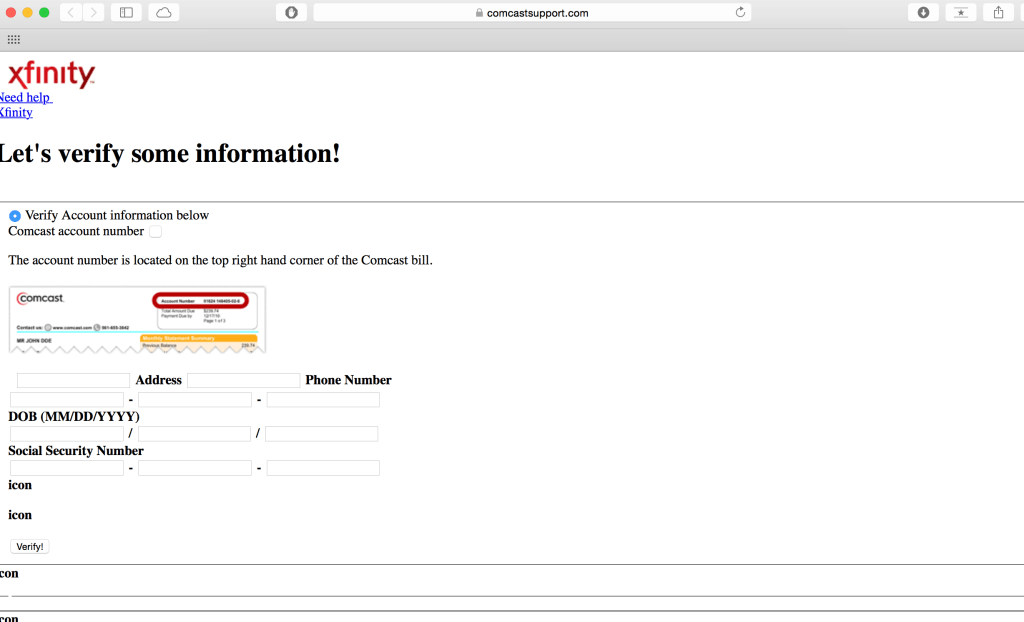
“We successfully replicated Comcast’s login page on our test site,” said Taylor. “We then injected this test page into the Comcast XSS to test the vulnerability further and it had indeed injected our html page from thug.org of the exact replicate of Comcast’s Sign-in page and Forgot Username Recovery page, which contains personal information.”
The exploit works by tricking a third-party service called Aptean SupportSoft into displaying code from outside of the main, secure domain. By “calling” the outside server, SupportSoft allows hackers to inject nearly any code into the customer service system, including JavaScript alerts.
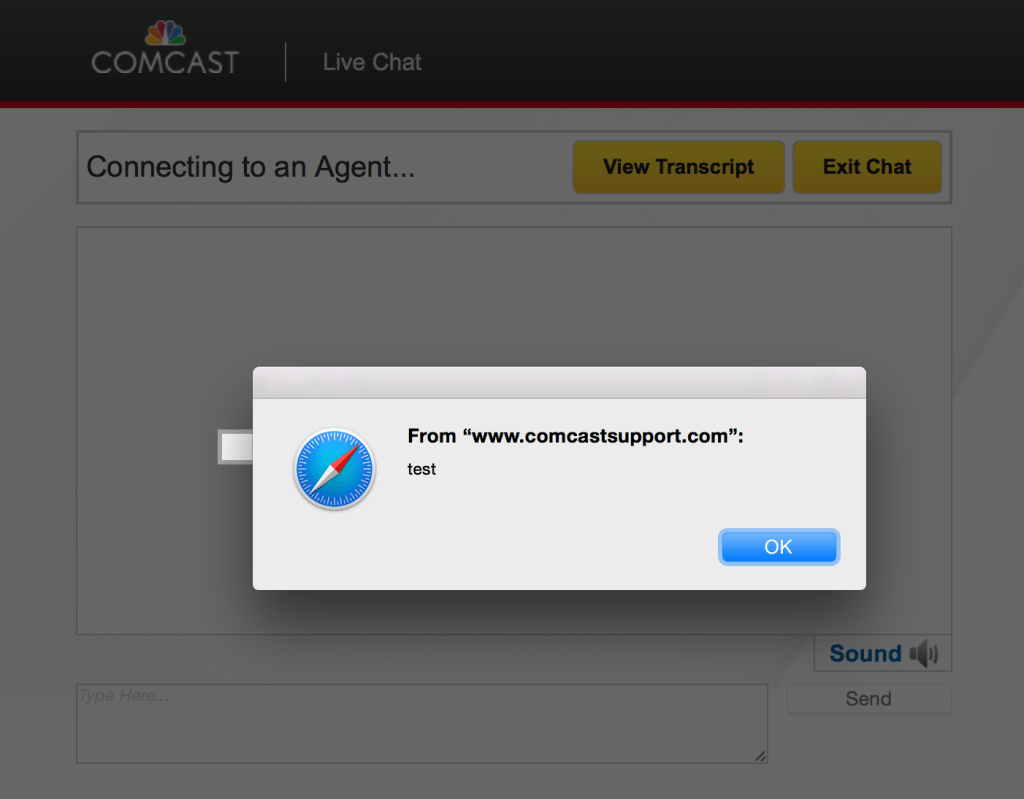
Aptean’s own support system is hidden behind a login screen but the vast majority of these implementations are open and vulnerable to attack.
I’ve contacted Aptean and Comcast regarding the hole. Comcast is repairing it but Aptean has not yet replied. UPDATEL Aptean repaired the hole in early August.



