The role of QUERLO in the INFORMATION DRIVE involving INTERNET PRIVACY, YAHOO! BREACHES and few of the most WANTED HACKERS in the history. - Part 1
This article is inspired by the recent announcement of Micky regarding Internet Privacy, QUERLO and Yahoo! Breaches. Actually as of the writing of this blog I already submitted one related blog waiting for review. I hope I could get good ratings although if not then it’s alright since I still get extra buzz scores for sure regardless of the number of stars I could get. Click here to see the latest Content Review update: New Daily Quest and More Buzz Bonus Rewards.
I had been discussing about Internet Privacy, Yahoo! Breaches and QUERLO in my previous blog although I will do the same here with little modifications of course, but I will also include the top most wanted computer criminals in the U.S. history, since we are talking about hackers here, at least we will understand and be able to see the whole picture specially me who isn’t a computer wizard at all. Perhaps looking up to the identities of those hackers would somehow help us comprehend why they do it and what benefit they could get in doing prohibited acts.

Photo Credit: Consumer Affairs via https://www.consumeraffairs.com
In my research I learned for the first time that not all hackers are bad. I mean there are hackers with good intention although from the word hackers alone, they still are violating some privacy. Anyhow it did sounds confusing but we will learn more as we go on with this blog. So continue reading.
The good hackers are called “white-hat hackers” the purpose of their action is to improve computer security. There are also hackers who are doing it just for the sake of fun, meaning they are having fun when they hack and they are called “gray-hat hackers”. But the malicious kind who intrude someone else privacy in exchange of money or simply with evil intentions, they’re called “black-hat hackers”. These black-hat hackers can cause serious harm and damage and one of their victims are the billions users of Yahoo! who were affected in the series of breaches that happened in the years 2013 and 2014.
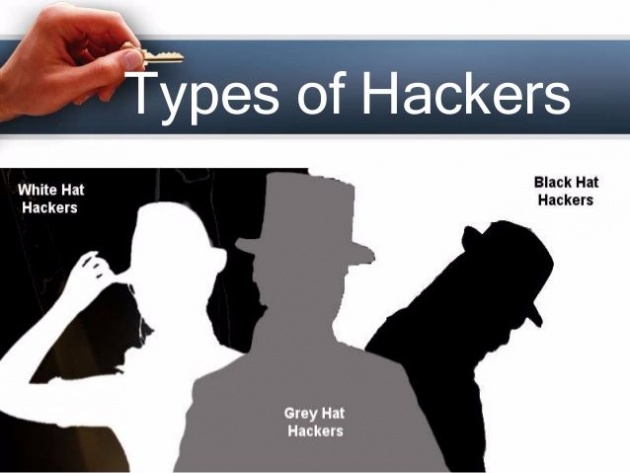
Photo Credit: https://www.slideshare.net
Yahoo! breaches
In 2016, Yahoo! an internet service company reported two major data breach, the first happened in 2014 which affected more than 500 million Yahoo! users accounts. The second data breach happened in 2013 which affected more than 1 billion Yahoo! users accounts.
The first reported data breach in 2016 had taken place sometime in late 2014, according to Yahoo! the hackers had obtained data from over 500 million user accounts, including account names, email addresses, telephone numbers, dates of birth, hashed passwords, and in some cases, encrypted or unencrypted security questions and answers. Security experts noted that the majority of Yahoo!'s passwords used the bcrypt hashing algorithm which is considered difficult to crack, the rest used the older MD5 algorithm which can be broken rather quickly. – Wikipedia
Another data breach occurred on Yahoo! servers in August 2013; Yahoo! stated this was a separate breach from the late 2014 one and was conducted by an "unauthorized third party". Similar data as from the late 2014 breach had been taken from over 1 billion user accounts, including unencrypted security questions and answers. Yahoo! reported the breach on December 14, 2016, and forced all affected users to change passwords, and to reenter any unencrypted security questions and answers to make them encrypted in the future. In February 2017, Yahoo! notified some users that data from the breach and forged cookies could have been used to access these accounts. This breach is now considered the largest known breach of its kind on the Internet. - Wikipedia
Video Credit: ABC NEWS via www.youtube.com
If you notice, both incidents were reported late and such late disclosure of the two major illegal intrusion to Yahoo! internet privacy caused them to be criticized and even face several legal complaints and until now still under investigation.
Now, considering all those points above, I find the need of Yahoo! to avail of the benefits QUERLO, a chatbot with a human touch could provide. That is to disseminate relevant information to its users and be able to give them warning in just a very short time.
So what are the things QUERLO is capable to do to help find solutions on problems like this?
Please read below important points about QUERLO, taken from their official website, www.querlo.com
Querlo is a consulting firm that provides “Emotional Chatbot" solutions and data management aimed to support businesses in the use and humanization of Artificial Intelligence. - www.querlo.com
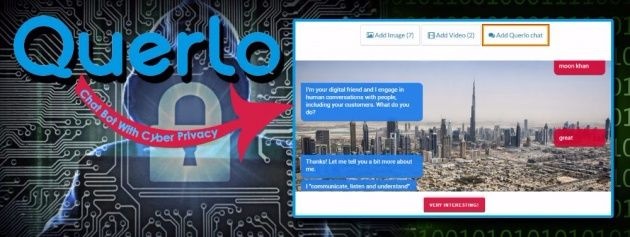
With Querlo’s Emotional Chatbot solutions, people are engaging in confidential one-on-one conversation in protected environments, motivated to share truthful conversations. - www.querlo.com
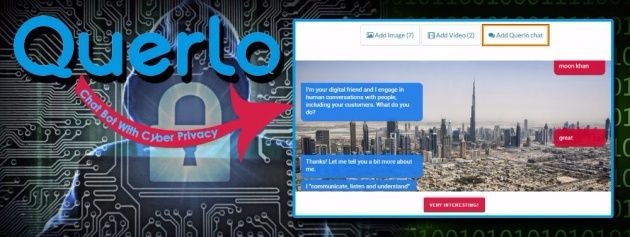
A team of hands-on experts that in the last 3 years, strategized, designed and launched 800+ Chatbots, collecting over 5 million items of data for clients including HSBC, Tetra Pak, Philip Morris and Yomiuri Shimbun – to name a few. - www.querlo.com
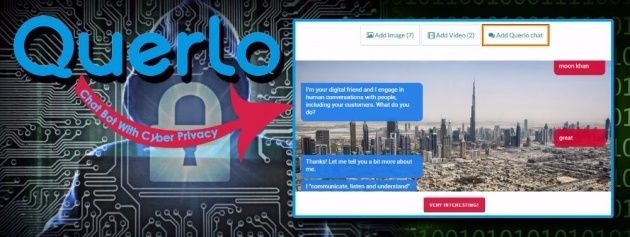
Querlo is part of MTI USA inc, established in New York in 1995 owned and operated by a team of Italian technologists with offices in USA, Europe, Asia and Middle East. - www.querlo.com

This is a detailed explanation/presentation about how QUERLO works, watch and appreciate yourself how wonderful this technology is!
Video Credit: Shy High Advertising via www.youtube.com
To know more about QUERLO please participate in the survey chat below:
TOP 10 NOTORIOUS HACKERS IN THE WORLD

Photo Credit: https://busybee4u.blogspot.com
Since we are talking about hacking and internet privacy let us check the 10 most wanted hackers in the history, what they did and what happen to them after committing the biggest mistake in their lives. Does such action made their lives better? Let's find out!
1. Kevin Mitnick
Number one in the list is Kevin Mitnick, an American computer security consultant, author and hacker, he was named as the “most wanted computer criminal in U.S. history”. Kevin Mitnick is very famous during that time such that his story inspired one writer, his story eventually become a movie entitled Track Down which was released in 2000.
What did he do?
Kevin Mitnick served a total of 6 years in prison, he was caught and convicted twice. He was convicted of hacking the Digital Equipment Corporation’s network, breaching the National Defense warning system and stealing corporate secrets.
Where is he now?
After fully serving 6 years, Kevin Mitnick became a consultant and public speaker for computer security. Currently he runs Mitnick Security Consulting, LLC.

Photo Credit: The Hacker News via http://thehackernews.com
2. Jonathan James
Second is Jonathan James. Jonathan commonly known as “comrade” is a native of South Florida and was only 15 years old when he committed his first offense. This American hacker was the first juvenile imprisoned for cybercrime in the United States.
What did he do?
Jonathan James was able to make a series of intrusions into various systems and the most renowned is that he was able to hack NASA’s network which caused damaged equaling to $1.7 million. Because of that NASA had to shut down its network for three weeks while they investigated the breach, which cost them an additional $41,000 just to check and fix their system.
Where is he now?
The story of James is somewhat tragic, he was caged even if he was still a minor and later in 2008 he committed suicide. According to the reports, he kill himself (using a gun) because he fears that he might be convicted with more crimes that he didn’t commit.

Photo Credit: TechWorm via https://www.techworm.net
3. Albert Gonzalez
Third is Albert Gonzalez. He was born in America in 1981. Albert is a computer hacker who was accused of being the leader of the combined credit card theft and reselling of more than 170 million card and atm numbers. Their group was called “ShadowCrew”.
According to Wikipedia, Gonzalez and his accomplices used SQL injection to deploy backdoors on several corporate systems in order to launch packet sniffing (specifically, ARP Spoofing) attacks which allowed him to steal computer data from internal corporate networks.
What did he do?
Albert Gonzalez spearheaded the stealing and selling of credit card numbers. He collected more than 170 million credit card and ATM card numbers in just 2 years. Their group also fabricated fraudulent passports, health insurance cards, and birth certificates for identity theft crimes.
Where is he now?
Albert Gonzalez was penalized to prison for 20 years and is scheduled for release in 2025. 8 more years and he can do the crime again if he wants to (LOL).
4. Kevin Poulsen
Fourth in the list is “Dark Dante” with legal name Kevin Poulsen. He was the first American to be released from prison (after 5 years) with a court sentence that barred him from using computers and the internet for 3 years after his prison sentence.
What did he do?
One of the things that he did was taking over a radio station’s phone lines and fixed himself as the winning caller for a brand new Porsche. He also hacked federal systems and stole wiretap information.
Where is he now?
After service his sentence he work as a journalist and later became a senior editor for Wired News. In 2006, he was able to help law enforcement to identify sex offenders on MySpace.
In October 2006, Poulsen released information detailing his successful search for registered sex offenders using MySpace to solicit sex from children. His work identified 744 registered people with MySpace profiles and led to the arrest of one, Andrew Lubrano. - Wikipedia
So there we go with the first part of this blog, I hope you learn something. Watch out for the second part where I will be talking about the other 6 famous hackers and continue to discuss about the amazing technology QUERLO, a chatbot with a human touch and few updates about Yahoo! breaches and Internet Privacy.
By: TRB - A father of 5, an Overseas Filipino Worker and willing to be part of the worldwide campaign against poverty, climate change, and inequality.




