image Credit: @artbytes via bitlanders
12 Tips How To Avoid Online Threats
How To Protect Yourself From Online Threats -Part 2
In the first part of this series (How to Protect Yourself From Online Threats- Part 1)I explained how everyone could be exposed to various online threats. Once you get connected to the Internet, you are exposed to any of the threats that loom online.
In this part, I will share with you some 12 on how to cut your exposure to these online threats.
Before that, I would like to emphasize that it is necessary to install reliable cyber security software or apps. This you need to install an anti-malware and a firewall on your device. But having an antivirus and firewall is not an assurance that your system will not be infected.
What should you do?
Don't Expose Yourself To Online Threats.
Installing cybersecurity software is a good precaution. Yet, there are new threats and variations of existing threats that come up every day. These new variants are often capable of avoiding detection.
Thus the things you do on the Internet could minimize your exposure to these online threats. But, you increase your exposure if you are not careful.

You don't run on an open field with an open umbrella during a thunderstorm.
Image Credit: BrinWeins via Pixabay
Avoidance is your first line of defense against threats.
12 Tips How to Avoid online threats.
Here are 12 Tips on how to avoid online threats.
1. Don't Download Attachments From People You Don't Know!
Trojan Horses, Spyware, and other malware are downloaded this way. The cybercriminals will send you email or messages with interesting or intriguing subjects. It could come with a funny picture or video, a game or other interesting software or app… These are baits.
Once you download the attachment, sometimes nothing visible happens. Sometimes you get the picture or video. But on the background, it could download something else without you knowing it. For sure it's a trojan horse that could open up a backdoor to your computer. If it's a software, it is most likely a trojan horse.
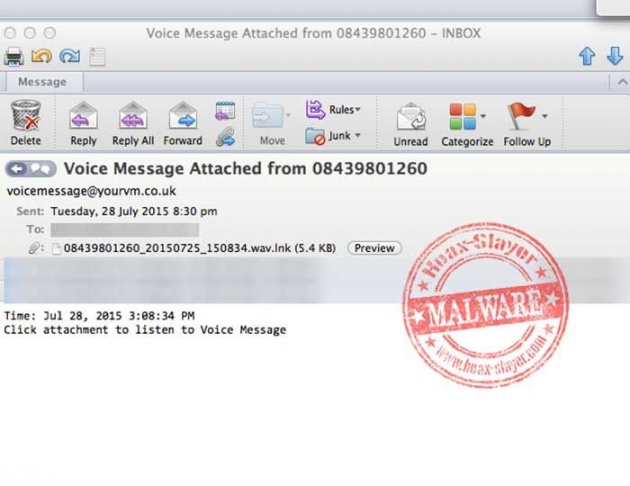
Image Credit: Hoax-Slayer.Net
2. Don't click links from messages sent by people you don't know
The first step in Phishing is sending messages to all email addresses they could get. From these links, you can be lead to a number of threats.
- Phishing - the image below is an example of a message containing a link to a phishing site.
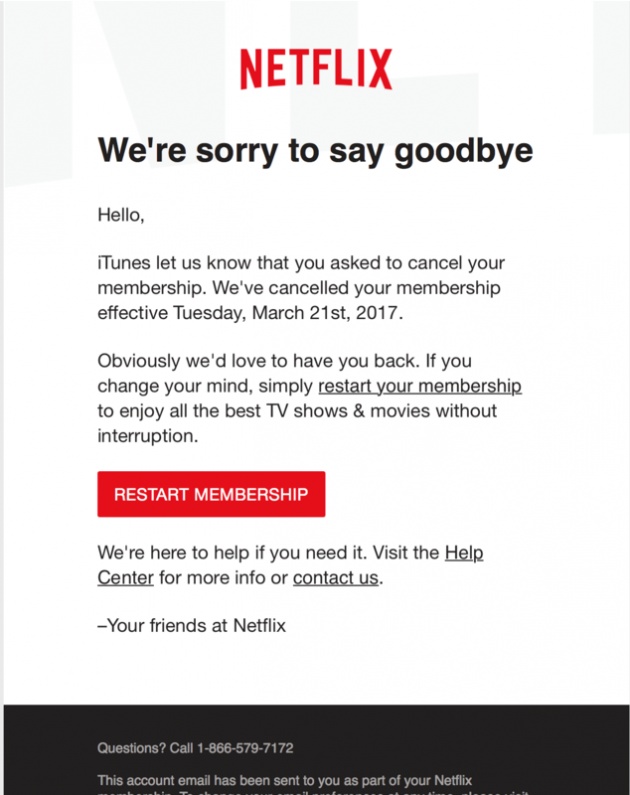
Image Credit: CoolMomTech.Com
This is an example of DEACTIVATION Scare. The message says that the user's membership has been CANCELLED. It asks the user to RESTART the member's NetFlix account. Most likely if the user clicks the link it will lead to a phishing site. In this case, the site will appear exactly like the official Netflix site, complete with the online membership form.
That form would include payment method, in which the user needs to enter his/her credit card information. After completing the form, the user will simply be redirected to the legitimate site. BUT, the cybercriminals already got his/her credit card information
. - Trojan Horse and Other Malware. The link could contain a script that will download a trojan horse or other malware without you knowing it.
How To Avoid These Threats
There is one sure way to avoid these types of scam. DON'T CLICK THE LINK from the message. Rather, type the Netflix address or the URL of the site manually. There you will see if your account has been truly canceled or not.
3. Minimize Social Logins
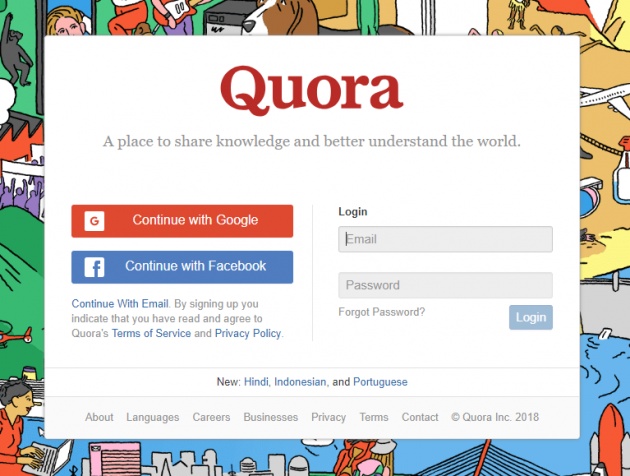
some sites like Quora.com allows you to use other social networks to log in to their site.
Image Credit: @artbytes via Bitlanders
Honestly speaking, I am quite guilty of this one. Social Logins or logins using your existing email, Facebook, Twitter or any other social media account is very convenient. You don't have to create a new login name and password. Thus you don't have to remember another set of username and password.
However, you will be giving some of these sites access to some of your personal information. Some will ask permission to access your contact list.
Another danger for using social logins too much is, when the account you used is hacked, your other accounts can be accessed easily as well.
4. Don't put too much personal information and pictures on social networks.
Putting too much personal information and letting the public see them will put you beyond the online threats. Criminals would know where you live, your phone numbers, the names of your family members, etc… thus you and your family can be targeted for physical crimes like robbery.
As much as possible don't put these pieces of information:
- Home address
- home phone number
- cell phone number
- names of parents and siblings
- name of your school
If you must, post them, configure your privacy settings that only your close friends and family members can see them.
5. Don't add strangers as friends on social network.
Unless you have an online business or you are a blogger, avoid adding strangers to your friends' list. You may never know that one or two of these strangers are fake accounts of cybercriminals looking for unsuspecting victims.
Here's a news video on 'Online RomanceScam'
Video Credit: CBS via YoutTube
6. Avoid Visiting Porn Sites.

Image Credit; @artbytes via Bitlanders
Most porn sites are breeding grounds of malware and other forms of threats. It's a minefield of "Click-Jacks". Almost everytime you click anywhere within a porn site will open an ad and probably something else. That something else could be a script that could download any form of malware.
7. Download software or apps from trusted sources only
Avoid downloading software and apps from torrent sites. Most of the software available on Torrent sites are probably:
- cracked - In which the security features of that software may have been disabled.
- Cannot be updated - if it's cracked, it can't be updated. Meaning you cannot get the necessary security patches of that software.
- infected with a virus. You will never know it but the source could be infected with a virus or A malware.
For Windows, download from trusted sites like file Hippo, Download.com or other sites referred to by the software developers. Here's an article with a list of trusted download sites: www.makeuseof.com/tag/9-cleanest-safest-websites-download-free-software-windows/
For Android, download only from Google's Play store and for iPhone and iPads, get the apps from iTunes or AppStore.
8. Don't be afraid if a website says your system is infected.
One method cybercriminals use is to scare the Internet users. While browsing, a message would pop-up with a warning that your system is infected by a number of virus and malware.
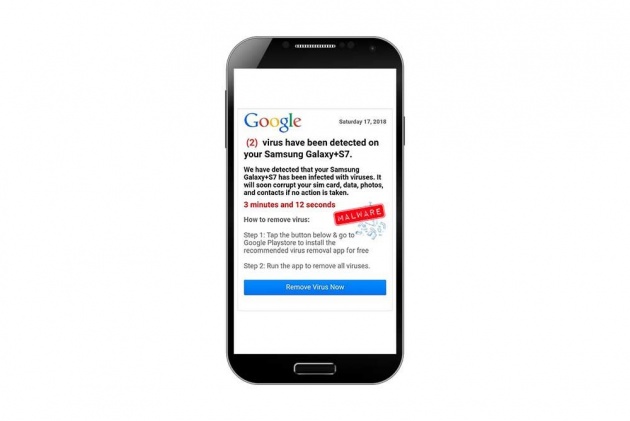
Image Credit: Hoax-Slayer.Net
Again DON'T CLICK THAT LINK!
9. Use Strong Password
Here is a YouTube Video that teaches how to create a strong password.
Video Credit: @Safety in Canada via YouTube
10. Use Incognito tab whenever you are using a public computer.
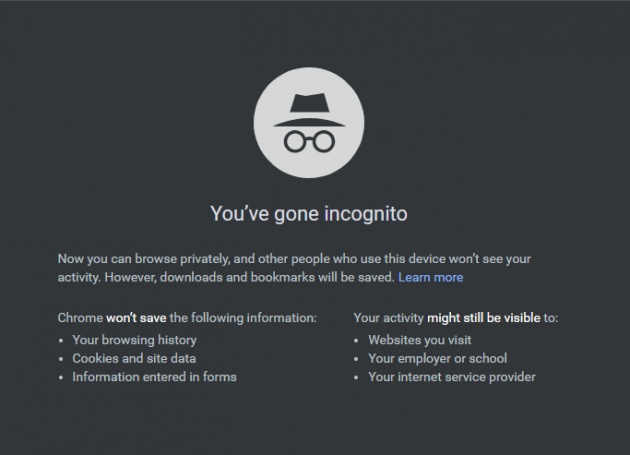
Image Credit: @artbytes for bitLanders
Whenever you use a publicly used computer like in an Internet Cafe or school laboratory, always use the Incognito tab or Private tab. Using Incognito will automatically delete all information that you entered including your username, password once you close the browser. This way even if you forgot to log out your Facebook, you are automatically logged out once the browser is closed.
For Chrome, press CTRL+SHIFT-N to open a new Incognito tab.
11. Beware of FREE Wi-Fi Access.

Image Credit: @geralt via Pixabay
Free wi-fi is cool! However, some cybercriminals may be scanning the wi-fi access and looking for a vulnerable device.
Also if find a free wifi in the middle of nowhere, beware. It could have been set-up to gather information from the users.
12. Avoid using an Administrative account on your computer
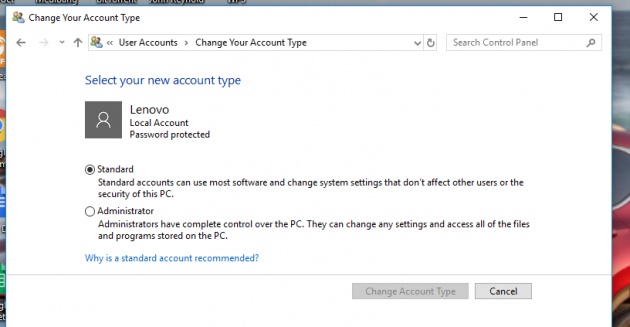
Image Credit: @artbytes via Bitlanders
Last but not least. Avoid using the Administrative account on your Windows computer. I admit this does not help you avoid those threats. Bu this will increase the level of security on your Windows computer.
Using a standard user means, you don't have the right to install anything. When a trojan horse or a web-script install something into your computer it will ask your permission to install it with the Administrator account and password.
Honestly speaking, there is no 100% assurance that you are safe on the Internet. However, following these actions, increases your chance to avoid becoming a target of cybercriminals.
The next part, I will discuss how to maximize the security features of security software.
Thanks for reading
-o-o-O-O-O-0-0-0-O-O-O-o-o-
John Reynold Loberiza (a.k.a @artbytes) is a freelance graphic artist, web developer, and blogger. He is also a licensed Financial Adviser under Insular Life.
The content of this blog post is the author's original work. Proper credit is always given to the respective sources of information and images. Please feel free to check out my other blog posts: http://www.bitlanders.com/Artbytes/blog_post
If you have any reactions or inquiries regarding the subject of this post, please write it in the comment or send the author a private message.
For more information or questions you can also:
Follow me on Twitter: http://twitter.com/jrlcentral
or email me at jrlcreativeideas@gmail.com
~°~°~°o0O0o°~°~°~
If you are not a member of Bitlanders yet and you are a content creator- a writer, blogger, photographer, an artist or a hobbyist, you can earn from your creations (blog posts, photos, artworks, or videos) by uploading them in Bitlanders.
Join Bitlanders
You can join Bitlanders by clicking this link-> http://bit.ly/Join_bitlanders




