Monday, September 08, 2014
So far, we all are well aware of the fact that Chinese have had a past filled with cases of Cyber Crime. China is the world’s largest exporter of IT goods, but it has been criticized by many countries due to suspected backdoors in its products, including United States which has banned its several major government departments, including NASA, Justice and Commerce Departments, from purchasing Chinese products and computer technology. The new exposure indicates the same.
Chinese Government is running a man-in-the-middle (MitM) cyber attack campaign on SSL encrypted traffic between the country’s education network and Google.
In an effort to monitor its users of China Education and Research Network (CERNET), Chinese authorities has started intercepting encrypted traffic to and from Google’s servers, the non-profit organization GreatFire reported on Thursday.
However, just like many other foreign websites, Google is blocked in China. Because Google is one of the vast and valuable website for research purpose, Chinese authorities allow access to it through CERNET, a nationwide education and research computer network.
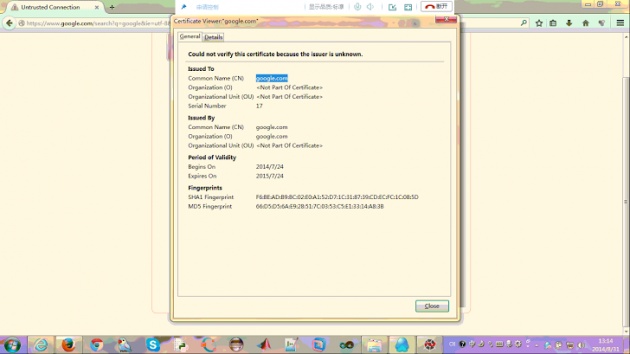
The story broke when CERNET users started reporting on social media websites that they are receiving warning messages about invalid SSL certificates when they try to access google.com and google.com.hk through CERNET.
According to the non profit organisation GreatFire, the Chinese authorities have launched a man-in-the-middle (MitM) attack against the encrypted traffic between CERNET and Google in an effort to control the media as well as messages on all fronts.
The present authorities feel that blocking Google might receive an angry rebuttal from students, researchers, and educators throughout the country, so MitM attack will solve the purpose.
“Instead of just outright blocking Google on CERNET, which would have raised the ire of students, educators and researchers across China, the authorities felt that a MITM attack would serve their purpose. By placing a man-in-the-middle, the authorities can continue to provide students and researchers access to Google while eavesdropping or blocking selective search queries and results,” GreatFire reported in a blog post."
With the help of MitM attack, Chinese authorities were spying on users’ search queries and their results. GreatFire said that they concluded the result after following the expert advice from Netresec, a security-based company that analyzed the MITM attacks on Github.
Until last month, CERNET users could able to access the search engine Google freely, but after 28 August, there have been changes and users receive a certificate expiration page warnings when they search for something.
Experts believe that the devices which are performing MitM attack may be injecting packets near the outer border of CERNET, the place where it peers with external networks. However, Netresec researchers said that it’s difficult to figure out how the attack was planned, but DNS spoofing was certainly not used.
“It’s difficult to say exactly how the MITM attack was carried out, but we can dismiss DNS spoofing as the used method. A more probable method would be IP hijacking; either through a BGP prefix hijacking or some form of packet injection. However, regardless of how they did it the attacker would be able to decrypt and inspect the traffic going to Google,” Netresec researchers noted in a blog post."