
Security researchers have discovered a new strain of malware that makes use of extraordinary measures to evade detection and analysis, making the computer it infects unusable.
Dubbed Rombertik, which is "unique" among other self-destructing malware samples due to its unique evasion techniques. As soon as any analysis tool is detected, Rombertik attempts to delete the device's Master Boot Record (MBR) and home directories, making the machine constantly restart.
Rombertik is a complex piece of spyware designed to "indiscriminately" collect everything a user does online in order to obtain victim’s login credentials and other confidential information.
Infects users via Phishing campaign:
Rombertik typically gets installed on vulnerable machines when users click on malicious attachments included in phishing emails, Cisco security researchers Ben Baker and Alex Chiu said in a blog post Monday.
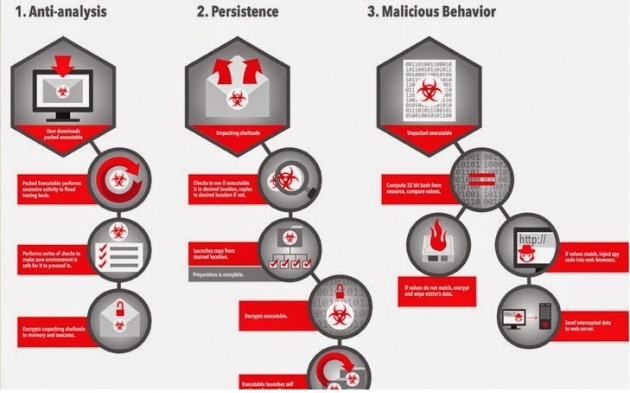
Once loaded into the system, Rombertik first runs a series of anti-analysis checks to determine if it is running within a sandbox.
In case it isn’t running within the sandbox, Rombertik decrypts and installs itself on the victim's machine, which then allows the malware to launch a second copy of itself and overwrite the second copy with the malware's core spying functionality.
Here’s the kicker:
After completing this process and before begins spying on users, Rombertik runs a final check to make sure it is not being analyzed in memory. In case it finds any indication of being analyzed, the spyware attempts to destroy the master boot record (MBR) of the vulnerable computer.
Rombertik then restarts the machine, and because now the MBR is missing from the hard drive, the victim’s computer will go into an endless restart loop.
MBR is the first sector of a computer’s hard drive that the system looks for before loading the operating system. However, deleting or destroying MBR involves re-installing of operating system, which means valuable data is lost.
In cases where the malware is under the microscope of security experts or any rival malware author, Rombertik will self-destruct itself, taking the contents of a victim's hard drive along with it.
Security researchers reverse-engineered the malware and found that Rombertik contains volumes of "garbage code" that have to be analyzed. The researchers were able to capture a small sample and found that…
...the unpacked Rombertik sample was 28KB in size while the packed version is 1264KB, including 75 images and 8,000 functions that are never used.
Rombertik other Tricks involve:
Moreover, Rombertik keeps itself in sandboxes by writing a random byte of data to memory 960 million times in an effort to overwhelm analysis tools that try to detect malware by logging system activity.
"If an analysis tool attempted to log all of the 960 million write instructions, the log would grow to over 100 gigabytes," researchers explained in a blog post.
"Even if the analysis environment was capable of handling a log that large, it would take over 25 minutes just to write that much data to a typical hard drive. This complicates the analysis."
Data wiping and Self-destructing malware:
Data wiping and self-destructing malware are not new. In last three years, we have seen a hike in malware evasion capabilities.
Wiper malware was used against South Korean banks and TV broadcasters in 2013 as well as against Sony Pictures Entertainment last year, which marked history in a massive data breach.
Also last year, the German Aerospace Centre was targeted by a self-destructive malware in an espionage attack, believed to be conducted by China.
TIP
The best way to keep your systems away from such malware is to have a best antivirus for PCs, as well as avoid opening malicious or suspicious links served via phishing emails.



