
More than 600 Million users of Samsung Galaxy smartphones, including the newly released Galaxy S6, are potentially vulnerable to a software bug that allows hackers to secretly monitor the phone's camera and microphone, read text messages and install malicious apps.
The vulnerability is due to a problem with the Samsung built-in keyboard app that enables easier predictive text.
One of the keyboard app version, SwiftKey IME, that comes prepackaged with Samsung's latest Galaxy smartphones could allow a malicious hacker to remotely execute code on user's phone even when if they are not using the keyboard app.
Users cannot get rid of this Flaw
The app cannot be uninstalled or disabled by the users of the Samsung smartphone devices, so it is up to Samsung to fix the critical bug.
The vulnerability was discovered by NowSecure mobile security researcher Ryan Welton, who notified Samsung about the bug in December last year.
The keyboard app periodically prompts a server whether it needs any updating, but Samsung devices do not encrypt the executable file, making it possible for any hacker to modify the traffic via an insecure Wi-Fi connection and send a malicious payload to a phone in order to gain control of it.
This process is usually known as a Man in the Middle or MITM attack, and encryption is often used to stop malicious hackers from exploiting them.
Swift has high privileges in the system, which means it can write files in a phone’s memory and can access most of its functions.
If exploited, the flaw could let an attacker to surreptitiously install malware on a user's smartphone; ac
cess the phone's microphone, camera and GPS; eavesdrop on text messages and calls; modify the behavior of other apps and even steal photographs and text messages from the phone.
The hacking attack was demonstrated Tuesday at the Blackhat security conference in London by Welton, and the video of his exploit is given below:
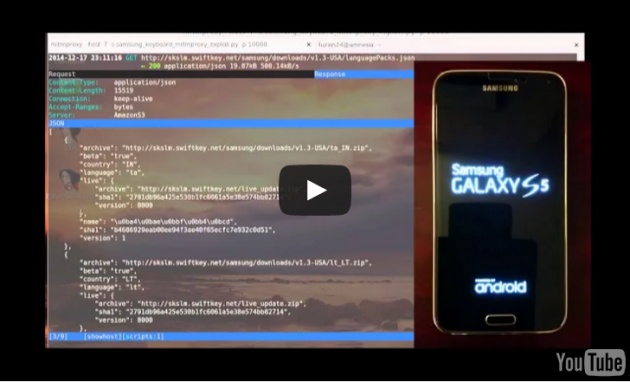
Affected Devices
There is a good news and a bad — The good news is that Samsung has started providing a fix to carrier network operators in early 2015, but the bad news is that the carriers have failed to offer security updates in a timely manner.
It is not known how many network operators actually provided the patches to their users, but the list of potentially vulnerable smartphone devices is a scary one.
The vulnerable devices include Samsung Galaxy S6, Galaxy S5, Galaxy S4 and Galaxy S4 mini on major United States carriers, including Verizon, AT&T, Sprint, and T-Mobile.
The Only Workaround:
As I said the vulnerable Keyboard app can not be uninstalled or disabled, so the only workaround for Galaxy handset owners is to stay away from unsecured Wi-Fi networks, until Samsung fixes the issue in a few days time.
The company said it will release a patch in the next few days, which will be accessible through its service Samsung Knox. The fix will be provided in the form of a security policy update that can be easily downloaded onto the smartphones.
"Samsung takes emerging security threats very seriously," the company said in a statement. Besides the security policy update, "we are also working with Swiftkey to address potential risks going forward."
Meanwhile, Swift said the flaw doesn't affect the SwiftKey applications on Google Play Store of Android or the iTunes App Store of Apple.
"We supply Samsung with the core technology that powers the word predictions in [Samsung] keyboard," Swift said. "It appears that the way this technology was integrated with Samsung devices introduced the security vulnerability."
Swift also claims the bug is "not easy to exploit." As in order to exploit this flaw, a user must be connected to a malicious wireless network and the user's keyboard is conducting a language update.



