
I have an Android phone with a five different gmail accounts configured in it. But what if any one of them get compromised via phishing, malware or any other way?
The Hacker would be able to access my Google account and obviously Google Play Store account too, which allows anyone to install any Android application remotely into my phone without my knowledge and confirmation…
What if someone compromises large number of Google accounts and trigger mass installation of a spying or malware app remotely with just one click????
Yes, this was exactly what the National Security Agency (NSA) had done under its widely spread Global surveillance program.
A new top-secret document obtained from the former NSA contractor Edward Snowden revealed that the NSA and its closest allies planned to hijack Google and Samsung app stores to infect smartphones with spyware.
The operation was launched by the Network Tradecraft Advancement Team, including spy agents from each of the countries in the so-called Five Eyes intelligence alliance — the United States, the United Kingdom, Canada, New Zealand and Australia.
According to the documents published Wednesday by CBC News in collaboration with The Intercept, the NSA, and the Five Eyes were working on ways to exploit smartphone technology for the purpose of surveillance.
PROJECT IRRITANT HORN
During the workshops held in Canada and Australia between November 2011 and February 2012, the Tradecraft unit dedicatedly looked for ways to find and hijack data links to servers used by Google and Samsung's mobile app stores.
As part of a project codenamed IRRITANT HORN, the team targeted app store servers where smartphone users get directed whenever they download or update any app from Google or Samsung app stores.
But why the Five Eyes alliance hijacking servers?
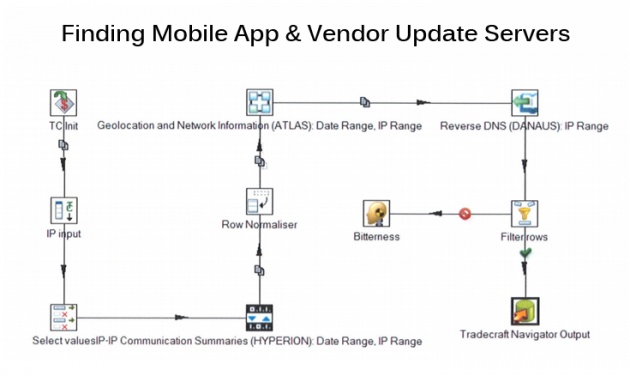
Simply, the team wanted to implant spyware on smartphones using man-in-the-middle attacks to infect the smartphones. The man-in-the-middle attack is a technique used by cyber criminals to intercept the communication and steal sensitive data passing through it.
In this case, the technique would have let the spy agencies modify the content of data packets transmitting between the targeted smartphones and the app store servers, ultimately inserting spyware on smartphones to take control of a person's device and covertly extract data from it.
Moreover, the spy agencies used its powerful Internet spying tool "XKeyScore" to identify targets by matching their targets' smartphones to their online activities, such as emails, chats and browsing histories in order to build the profiles of people they were tracking.
Exploited UC Browser Privacy Vulnerabilities:
Another major revelation from the documents was the spy agencies’ efforts to discover privacy flaws in one of the world's most popular mobile Internet browsers UC Browser — an app used to browse fast Internet across Asia, specifically in China and India with massive user base of half a Billion people.
The agencies tapped into UC Browser and exploited the weakness to collect data on suspected terrorists and other national intelligence targets, and in some cases, implant spyware on targeted smartphones.
When analyzed the Android version of the UC Browser app, it was found "major security and privacy issues" in its English and Chinese editions, putting millions of its users' data at risk, says a human rights and technology research group in Toronto, Citizen Lab.
National Security vs. Users’ Privacy
"Of course, the user of this application has no idea that this is going on," says Ron Deibert, director of the Citizen Lab. "They just assume when they open a browser that the browser's doing what it should do. But, in fact, it's leaking all this information."
The researchers have published their technical report detailing the many ways the UC Browser app has been leaking data, including SIM card numbers, search queries and unique device IDs that can be used to track people.
Deibert says the privacy vulnerabilities in the UC Browser not only exposed Millions of its users to surveillance carried out by government agencies, but it could also have been exploited by malicious hackers to harvest users’ personal data for years.
The problem is straight — by secretly exploiting privacy and security vulnerabilities in popular software for years, these spy agencies are putting ordinary users at risk.
These agencies are also making it easier for criminal hackers by opening loopholes, instead of reporting them to the companies so that they can be fixed on time.



