‘Hackers’ is currently one of the most popular cyberwarfare strategy online games on Android. 'Hackers' was developed by Trickster Arts and was released to the market (i.e. you can download the game on Android and iOs) in 2016. As the name implies, the gameplay mainly involves hacking and conquering other player’s system.
Hackers Join the Cyberworld - Android Gameplay Trailer (Video by Techzamazing)
And as one of the players of Hackers (though I’m currently new to the game), I will show you the short game guide dedicated for amateurs like me. Stay tuned to this beginner’s guide for Hackers as it will provide you some tips (not much on the cheats though) on the app.
Note: This guide is not a walkthrough. There are no hacks, glitches, cheats, etc. This guide will mainly teach you how to play Hackers.
The System
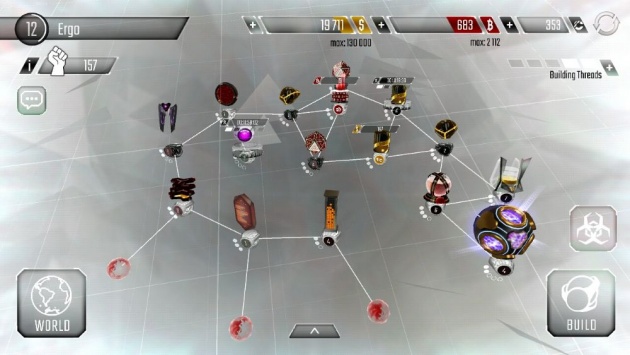
My Hackers System - Ergo (Screenshot Image by Haruo)
After you’ve made your account on Hackers, you will immediately be directed to the creation of the system. The system you are creating is similar to the one in real word; however, there are obviously twists in the game. You can build different nodes (i.e. facilities) which can help you strengthen your system. The nodes are divided into three categories (business, security, and hacking) and are as follows:
Business
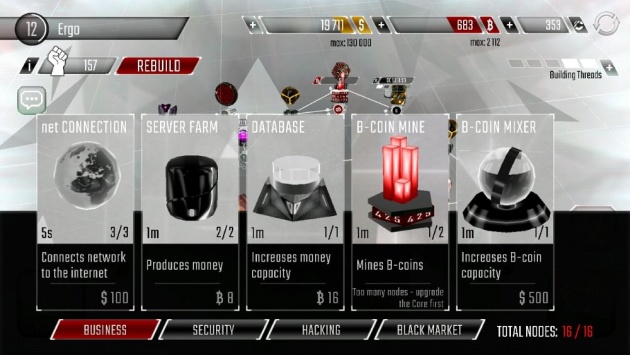
Business Nodes (Screenshot Image by Haruo)
- net Connection – Connects your network to the internet. All intrusions start from here. Higher levels of the Core may need more net Connections.
- Server Farm – The Server Farm hosts user services and resells computational power to produce money. Upgrade it to increase its production and capacity.
- Database – Databases store user accounts and bank accounts. Your money is managed and cleaned here. Upgrade the database to increase your max $ capacity.
- B-Coin Mine – This accelerated system mines B-coins - a cryptocurrency no hacker can work without. Upgrade it to increase the speed of B-coin production and capacity.
- B-Coin Mixer – Your B-coins are stored and cleaned here before you use them. Mixing B-coins together makes them (nearly) untraceable. Upgrade your Mixer to increase your B-coin capacity.
Security
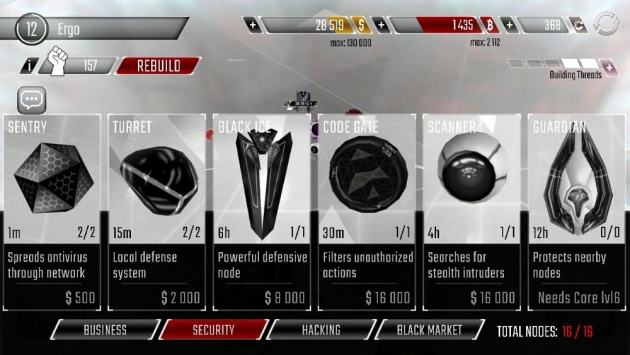
Security Nodes (Screenshot Image by Haruo)
- Sentry – Sentry is an antivirus that when activated copies itself to other nodes. It spreads fast and deletes enemy programs along the way. Upgrade it to make it stronger.
- Turret – A popular local defense system. It locates nearby hostile programs and focuses on them until they are deleted. To increase its strength, upgrade it to higher levels.
- Black ICE – Black ICE is a strong local security unit. The control of any hostile node can be taken over very fast. Upgrade it to increase its strength and firewall.
- Code Gate – A password protected gate is a great tool to slow down an attack. Code Gate massively reduces damage to its firewall but can be destroyed with a Battering Ram program.
- Scanner – Increases stealth program detection on all nodes three steps away and closer. Access, Wraith, and Portal programs alarm the network faster.
- Guardian – When an intrusion is detected, the Guardian starts installing protective subroutines on neighbor nodes.
Hacking
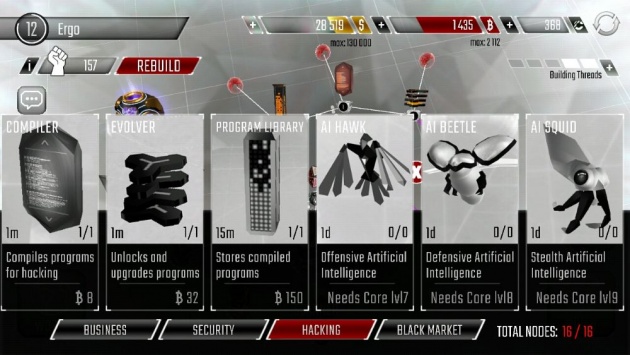
Hacking Nodes (Screenshot Image by Haruo)
- Compiler – All programs you will need are compiled here in the Compiler. Upgrade it to unlock more compiling threads and compile faster.
- Evolver – Smart evolutionary algorithms allows you to develop new programs and upgrade them to higher and better versions.
- Program Library - All your complex programs are stored in Libraries. Upgrade the Library to increase its capacity.
- AI Hawk – Once installed, the AI Hawk will periodically attack enemy nodes within three steps
- AI Beetle – Once installed, the AI Beetle will periodically repair the firewall of friendly nodes within three steps.
- AI Squid – Once installed, the AI Squid periodically disables enemy nodes within three steps.
Programs
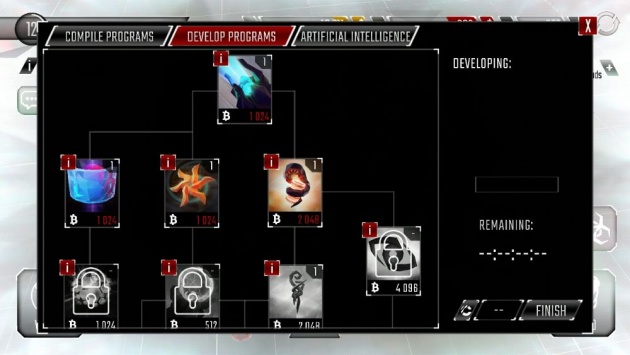
Develop Program for Hacking in Evolver (Screenshot Image by Haruo)
Hackers will never be complete with the hacking part itself. But before we delve into the hacking process, let us first arm ourselves with weapons – the programs we will need to hack another user’s system. There are numerous programs and some can only be unlocked after upgrading the Evolver. Anyways, each of those programs has their own functions. Here are the programs you can develop and use in the game:
- Beam Cannon – Basic program for any hacker. Beam Cannon attacks the strongest security nodes first.
- ICE-Wall – Fortify your nodes during attacks with the ICE-Wall defensive program. It absorbs enemy attacks until the ICE-Wall is destroyed.
- Shuriken – This offensive program spreads multiple attacks to all nearby enemy nodes.
- Data Leech – This greedy malware speeds up the downloading of money, B-coins, and Core databases. May be used even in stealth mode on nodes you have access to.
- Protector – Effective node protection with regeneration. Its randomized algorithm is used to protect nodes under constant pressure.
- Blaster – It takes time to install the Blaster, but once installed, it can quickly destroy firewalls. Plus, it freezes nodes for a short time.
- Worms – Worms’ primary trait is that they multiply. Install one and you’ll soon have many.
- Access – An essential program for stealth hacking. Access opens a connection to neighbor nodes and allows you to install Data Leech, Portal, and Wraith programs without raising an alarm immediately.
- Shocker – Freezes all neighbor nodes for a short time. Disabling security nodes buys you extra time to remove them.
- Battering Ram – There is nothing better to break through a gate then the Battering Ram program.
- Kraken – Release the Kraken! It monstrous tentacles come from net Connections and head straight towards the Core. The more tentacles together, the stronger the Kraken is.
- Wraith – Wraith silently disables the functionality of a node accessed by the Access program. Use Wraith to remove the largest threats on a target network.
- Maniac – This self-destruct kamikaze program deals massive damage to a targeted firewall. It’s usually enough to conquer a node in one blow.
- Portal – Make a backdoor connection in stealth node with the Portal program. A node with Portal installed becomes red. You may start your brute force attack from there.
Connecting and Hacking
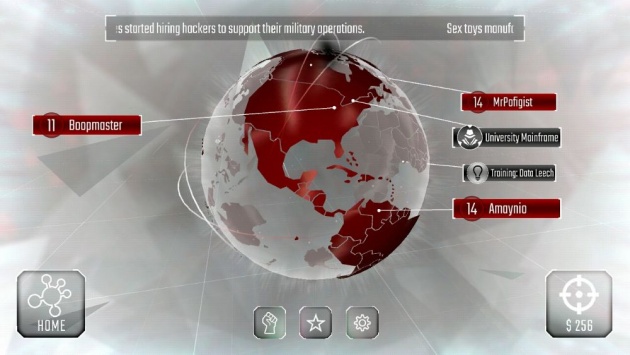
The World (Screenshot Image by Haruo)
In order to connect, you must first go to the World where you will be provided five systems around the world to choose from. Each of these systems has their own might so you might be careful in choosing who to attack. Fortunately, you are given some information on the system such as the level, number of wins and losses, and of course, the might. Therefore pick wisely among these systems.
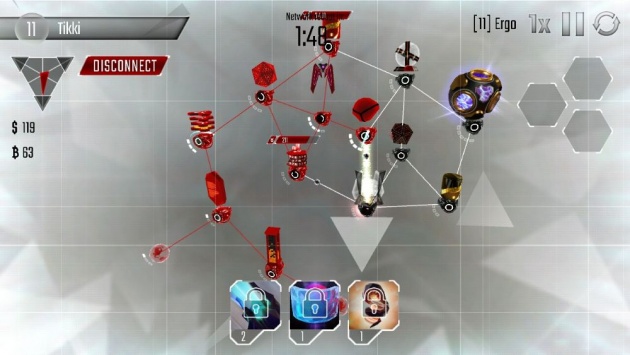
Attacking Another System (Screenshot Image by Haruo)
After you’ve chosen which system you are going to attack, the battle begins. As a beginner, I’ve never really use stealth hacking (but I will surely do that in the future) so the hacking I’m going to show you right now is the conventional one which most of the users on the game use.
Hackers Game = Kraken (Video by Maximumandroid - Just Good Games)
By clicking on the net Connection, you can select which and how many programs you will send out. The greater the number of programs you will send out, the faster and better the program can function. For beginner players, the most common problem will be the sentry which sends out antivirus throughout the system. The best solution to this problem is to hasten your hacking. Also, try conquering as many nodes as possible and keep out for the time. Your hacking will only be successful if you’ve downloaded the money and B-coins and downloaded the files in the Core databases.
Conclusion
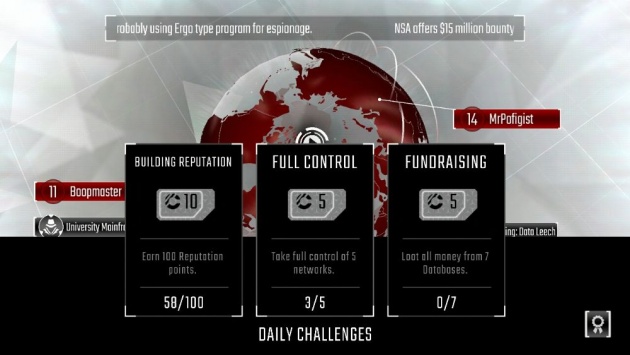
Daily Challenges for Free Credits (Screenshot Image by Haruo)
Hackers is a great game to play especially if you want to be a hacker wannabe. It’s fun and simple to play. Most of all, it’s completely free, unless you plan to buy credits (which can totally be gained in the game as well as free credits) and some other stuff. So I definitely recommend this game for you guys to try.



