Networks whose access is not controlled can not ensure privacy or data security that there are preserved and are not even able to prevent hackers from exploiting resources Network.
The efficiency achieved in communications through the Internet has caused a race to run networks directly through the Internet. The direct connections to networks Internet hackers facilitate the exploitation of resources of the networks themselves. When you connect a network to the Internet, in reality it connects directly to any other network connected to Internet.
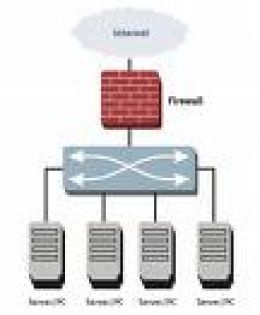
There is no central point of control of security. Firewalls are used to create control points on the border security of the networks. By managing the function routing between network and the Internet, firewalls inspect all communications passing between the two networks and allow or prohibit communications depending on their compliance with the policy security.
CHARACTERISTICS OF THE FIREWALL
Firewalls make more secure Internet connection because inspect and then accept or reject any attempt to link networks internal and external networks. Firewalls more comprehensive protect the network at every level software, datalink until the application. Firewalls acting at the points where access to other networks, being regarded as a "protection of the border. "This is an important concept, because, without it, every host on the network should perform the functions of personal firewall, consuming computing resources and overloading the network. Firewalls allow you to centralize all security services external machines that are optimized for that purpose and that this task exclusively. For them nature, firewalls create a "bottleneck" between the internal and external networks because all traffic that passes between networks must pass through a single point of control. This is a small price to pay in exchange for security.
Firewalls work mainly using three basic methods:
Packet filtering: to disable TCP / IP packets from unauthorized hosts and reject attempts not authorized connection services;
Network address traslation (NAT): to convert the IP addresses of internal hosts to hide them from external monitoring;
Proxy services: manage connections applications on behalf of internal hosts preventing any other level network connection between the host internal and external.
Many firewall also play two other important security services:
Encrypted authentication: allows users to the public network firewall to prove their identity in order to have access to the private network from external positions;
Virtual private networks (VPNs): establish a secure link between the two private networks over a public medium such as the Internet.
This allows physically separate networks using the Internet rather than communicating through external links on leased lines.
I FILTERS OF PACKAGES
The first were used firewall packet filters. Filters examine network protocols (such as IP) and transport protocols (such as TCP) on the basis of a set of rules and only those forward packages that conform to the criteria prescribed in their database of rules. Filters can be Implemented on the router or the TCP / IP servers. Filters implemented within router prevent trafficking suspect to achieve the destination network, while the software packet filtering TCP / IP servers can just avert a car involved responds traffic suspicion. Traffic continues to enter the network and could reach all computers inside. Filters usually follow the following rules:
block all attempts to connect inwards but at the same time allow those outwards to pass;
eliminate TCP packets directed to the ports that should not be available to Internet (such as ports for NetBIOS sessions), but allow access to packages that should go (SMTP). Most filters can specify exactly Which server should address a particular type of traffic, for example SMTP traffic on port 25 should go only to the IP address of a mail server; restricting access to the interior to a certain set of IP addresses.
Filters more sophisticated use certain algorithms to monitor the status of all connections through them, looking for signs Detector attempts to sabotage, such as source routing, ICMP redirection and IP spoofing. According to internal clients is generally allowed to create connections external host, and external host is usually prevented if only the start of attempts to connection. When an external host decides to start a TCP connection, it sends a TCP message to the IP address and port number of public server (eg pippo.com: 80). In starting message connection, it tells the server remotely what your IP address and what Port is ready to receive a reply. The external server sends data transmitting internal client reported at the door. When inspecting all traffic exchanged between the host, the firewall knows that Connection was initiated by an internal host connected to its interface, by IP address of the host, and as the host port expects to receive traffic back. The firewall then allow traffic to pass back to host previously addressed in the message IP connection to the internal host only through the designated door.
Filtering does not solve completely the problem of security on the Internet. First he IP addresses of places within the filters are present in traffic to the outside world, and this makes it easy to determine the type and the number of Internet hosts behind a filter, and consequently launch attacks against these addresses. The filters can not control all fragments of a message-based IP protocols higher, as in TCP headers, because the heading exists only in the first fragment. The following fragments not have any header information and can only be compared with the IP rules, which Usually inclined to allow traffic to pass through the filters.
FILTERING THE LEVEL OF OPERATING SYSTEM
Often it is not aware that most versions of Unix and Windows NT Server include packet filtering inside the TCP / IP protocol. This system filtering can be used in addition to a firewall external to control individually access to the server. As the only filtering is not sufficient to fully protect the network, filtering inside the operating system also is not sufficient to create a secure environment. In adding filtering offered by the operating system, should be setting the various functions system to ensure that the filters only allow transit of those protocols that are been explicitly authorized. Filtering based on the level of operating system allows you to define acceptance criteria for each card to the computer network for incoming connections intervening on the number of IP protocol, port number TCP, UDP port number. A typical server handles services listening on ports listed in the table.
The TCP / IP easy listening by following ports:
Port: 7 Services TCP / IP: echo
Port: 9 Services TCP / IP: discard
Port: 13 Services TCP / IP daytime
Port: 17 Services TCP / IP: quote of the day
Port: 19 Services TCP / IP: character generator
I usually listen to Internet services in the server from the following ports:
Port: 21 Internet Services: File Transfer Protocol (FTP)
Port: 23 Internet Services: Telnet
Port: 70 Internet Services: Gopher
Port: 80 Internet Services: World Wide Web (HTTP)
Port: 119 Internet Services: Net News (NNTP)
The file server hear from the following ports:
Port: 53 file servers Services: Domain Name Service
Port: 135 Services file server: PRC local Service (NT)
Port: 137 Services file server: Net BIOS Name Service (WINS only)
Port: 139 Services file server: NetBIOS Session Service
Port: 530 Services file server: LPR
Port: 515 Services file server: File Remote Procedure Call
The mail server hear from the following ports:
Port: 25 Services-mail address: SMTP, messages from the mail client to the server
Port: 110 Services mail: POP3, messages from the server to your mail client
Port: 143 Services-mail address: IMAP access by the client to the mail server
You should disable all protocols and addresses by default, and then set what services you want to host and support. Moreover, it should disable all possibilities of connection of external host on the network. By allowing this, hackers from grants open connections with the trojans or exploit flaws in software services. We must consider the possibility of filter and not respond to messages ICMP redirect and echo; block all packages showing signs of source routing TCP; block all protocols External routing (RIP, OSPF) access to the network; put the hosts for public services such as Web servers and SMTP outside packet filters rather than open holes through them.
NETWORK ADDRESS TRASLATION (NAT)
The NAT solves the problem hide internal hosts. NAT is fundamentally a service proxy: one host ago requests on behalf of internal hosts, so that conceal their identity the public network. Nat hides the internal IP addresses by converting all addresses of hosts interior at the firewall. The number of internal data packet is sent with the IP address Firewall, which in turn uses TCP port numbers to keep track of connections On the public and hosts on the private sector. It 'should be considered, however, that NAT being implemented only at the level TCP / IP, could go to the hidden information higher levels of service by exploiting vulnerabilities. And 'convenient to use a high level as a proxy to prevent a weakening of security levels high.
PROXY SERVICES
The network address translation solves many of the problems inherent in direct connections to Internet, but does not make quite sure the flow of datagrams through the firewall. And 'it possible for someone in possession of a network monitor the traffic exiting outwards and understand that the firewall is translating addresses for other machines. A hacker can also hijack connections or deceive TCP connections back to the firewall.
Proxies wide application prevent these problems. They can avoid completely switching protocols to the network level through the firewall and restrict the traffic only to the protocols highest level as HTTP, FTP and SMTP. Proxies remain pending attempts remote connection to the server and then replace the client query servers to achieve. The proxy application are different translators of network address and filters because the client application of the Internet is usually set and educated to talk with the proxy. For example, communicate to the Internet Explorer address of the web proxy server and it sends all web requests to the server rather than resolve the IP address and determine directly the connection. The proxy application should not be made about firewalls, and each server can run proxy role both within and outside the network. At least some kind of filter packages must be placed so as to protect the proxies that type of DoS attacks.
Ideally, the firewall can perform the function of proxies. This prevents packets coming from high public from being routed through the firewall. Some firewall proxy of office
Mask and filter the IPs, they can simply block attempts at direct connection externally (port 80 for HTTP) hosts rather than go to configure direct client software for the service proxy. The firewall proxy then connects to the server remote and requires data on behalf of clients locked. The data retrieved are returned to the client that he requested using transduction address firewall showing itself to the client throughout similar to the remote server. The proxy operating in this way are called transparent. Proxies defined security can perform content filtering for specific application level. For Examples HTTP proxy firewall seek HTML pages tags that relate to the applet activeX or removing the contents.
AUTHENTICATION ENCRYPTED
The encrypted authentication allows users external coming from the Internet to demonstrate a Firewall that they are licensed and therefore can open a connection to the internal network through the firewall. When the connection is established may or may not be encrypted according to Firewall product in use and if additional software was installed on the client to support the tunnelling. The use encrypted is appropriate because it occurs at the level of transportation between a client and the firewall. When the connection is open, everything normal application software and any software to access the operating system will run without obstacles, so you do not have to use special software packages that support your specific Firewall. However, the encrypted authentication reduces security firewall, as it introduces the following issues: the firewall must respond on some leads as expected of listening connection attempts, showing the existence of the firewall; the connection may be redirected using ICMP after creation, especially if it is not encrypted; a hacker who has monitored the connection might have the ability to simulate the address of client authorized to gain access to the network without any connection redirect existing; the authentication procedure may contain bugs allowing anyone on the Internet open holes through the firewall.
VIRTUAL PRIVATE NETWORKS (VPN)
The virtual private network (VPN) enables two separate networks to connect securely on Internet without exposing the data transferred. VPNs could still be subject to attempts hijacking or deception initial connection and any other kind of computer ambush while the tunnel is about to be put into operation. But when implemented as part of a firewall, authentication and other security services can be implemented for prevent attacks while the tunnel is about to be implanted. Once implemented, VPNs are so difficult to attack unti encryption remains secure. And since firewalls are in access point to the Internet, they represent the endpoints of the VPN. Then, the private networks traffic can transmitted as if they were two subnets in the same domain.
Typical Firewall Configuration